Last updated by: bg-11, Last updated on: 19/05/2025
Phase 4 – Additional security controls based on the CIS Foundations Benchmark guidelines
Document Creation: 05 May, 2025. Last Edited: 05 May, 2025. Authors: Bikendra Gurung.
Effective Date: 05 May, 2025. Expiry Date: 05 May, 2026.
Objective
The objective of this phase is to implement additional email security controls to further strengthen Redback Operations’ resilience against phishing, malware, spam, and other email-based threats. This implementation follows best practices aligned with the CIS Microsoft 365 Foundations Benchmark to ensure a secure, scalable, and compliant email infrastructure.
Deliverables
The following security controls have been implemented and validated using PowerShell scripts, which can be found in the ‘redback-cyber’ GitHub repository (link below):
Redback Cyber GitHub Repo - Additional CIS Security Controls - Email & Collaboration.ps1
| Control | Description | CIS Benchmark Ref |
|---|---|---|
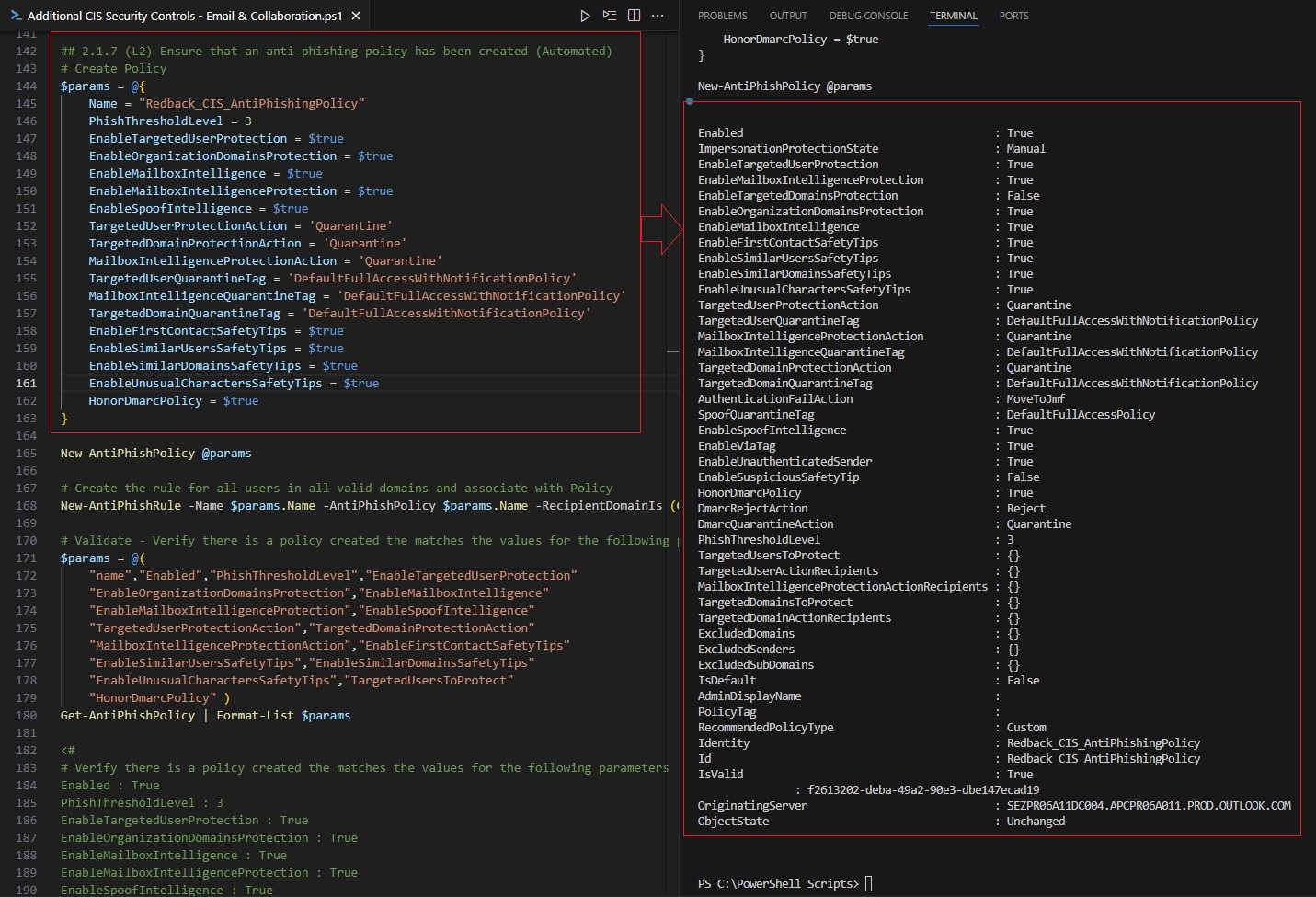
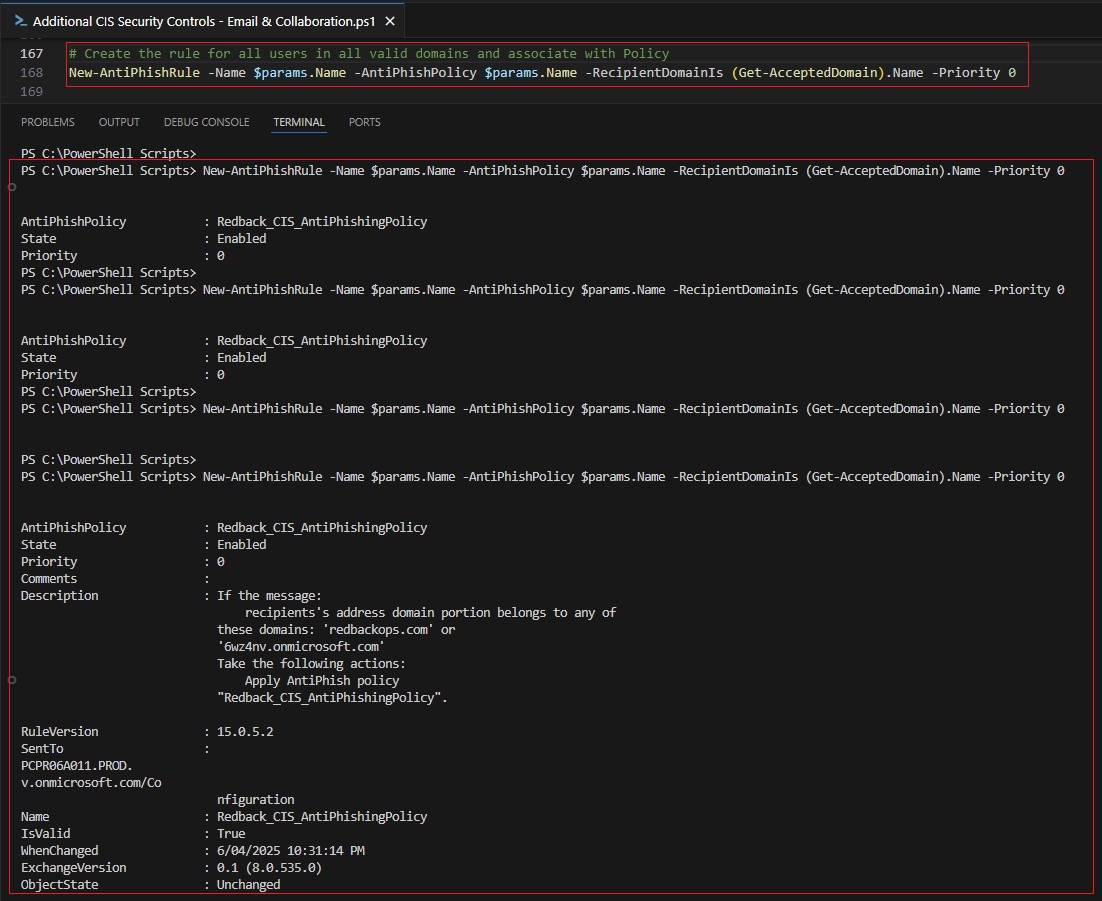
| Anti-Phishing Policy | This policy enables impersonation protection, spoof intelligence, DMARC enforcement, mailbox intelligence, and quarantine actions. | 2.1.7 |
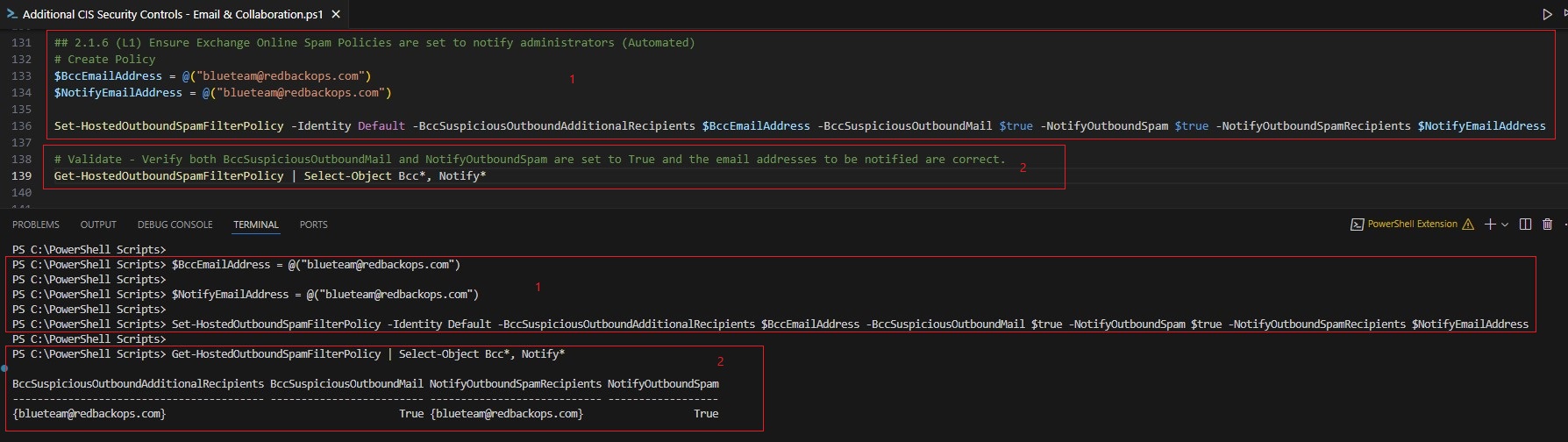
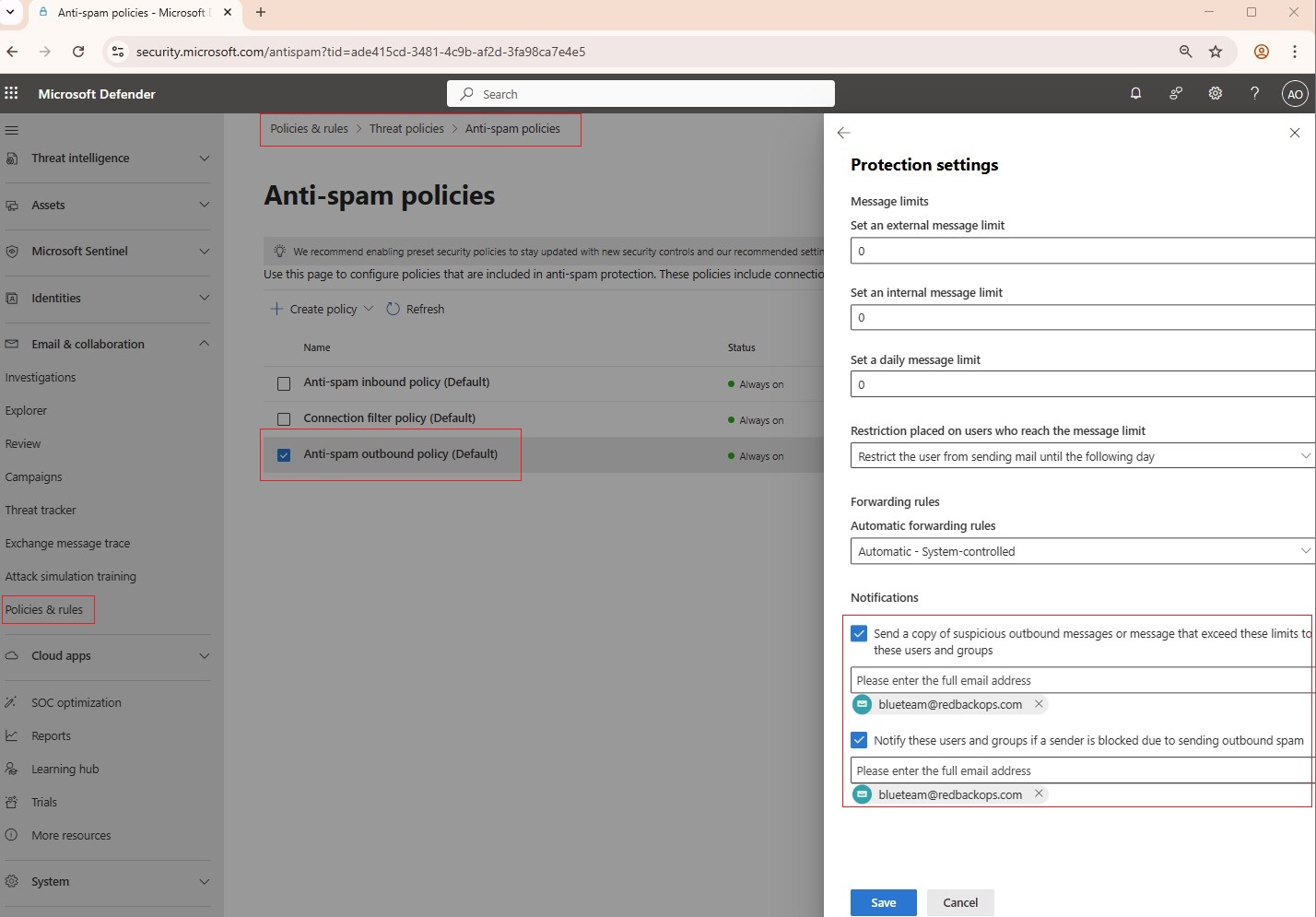
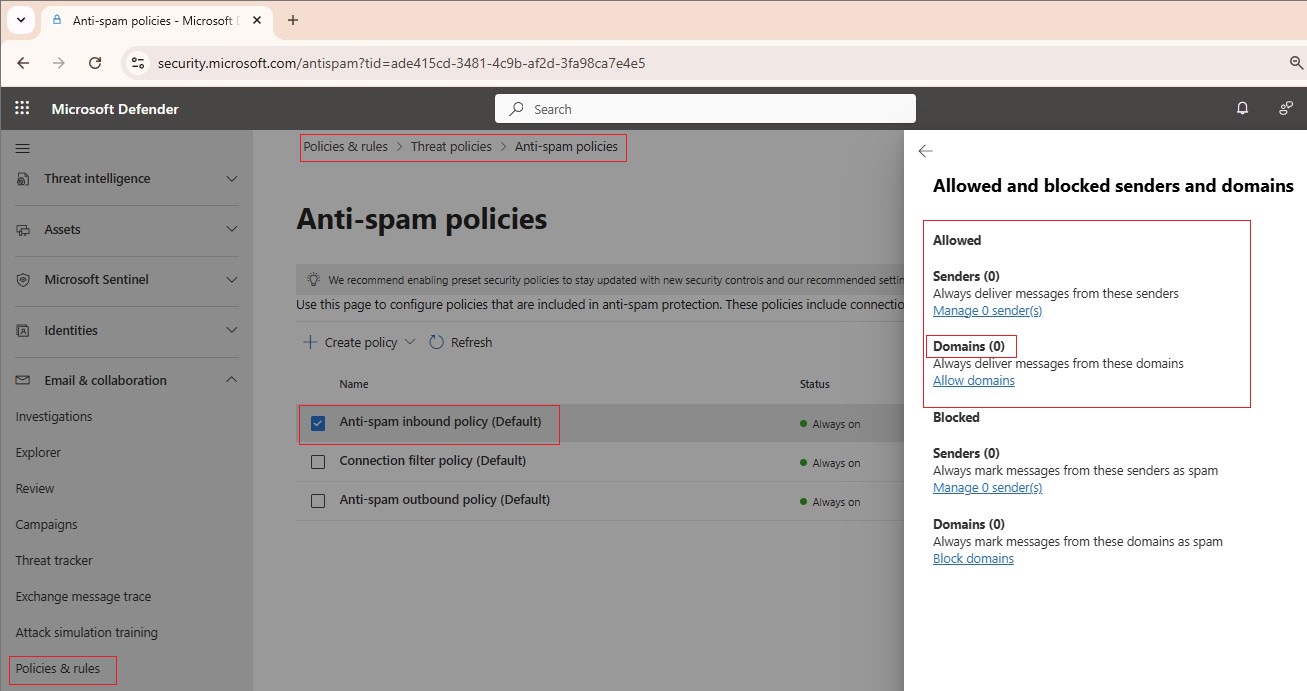
| Anti-Spam Policy | This policy: • Configures outbound spam filter to notify and alert administrators of suspicious outbound activities. • Ensures inbound anti-spam policies do not contain any allowed domains, preventing filter bypass. | 2.1.6, 2.1.14 |
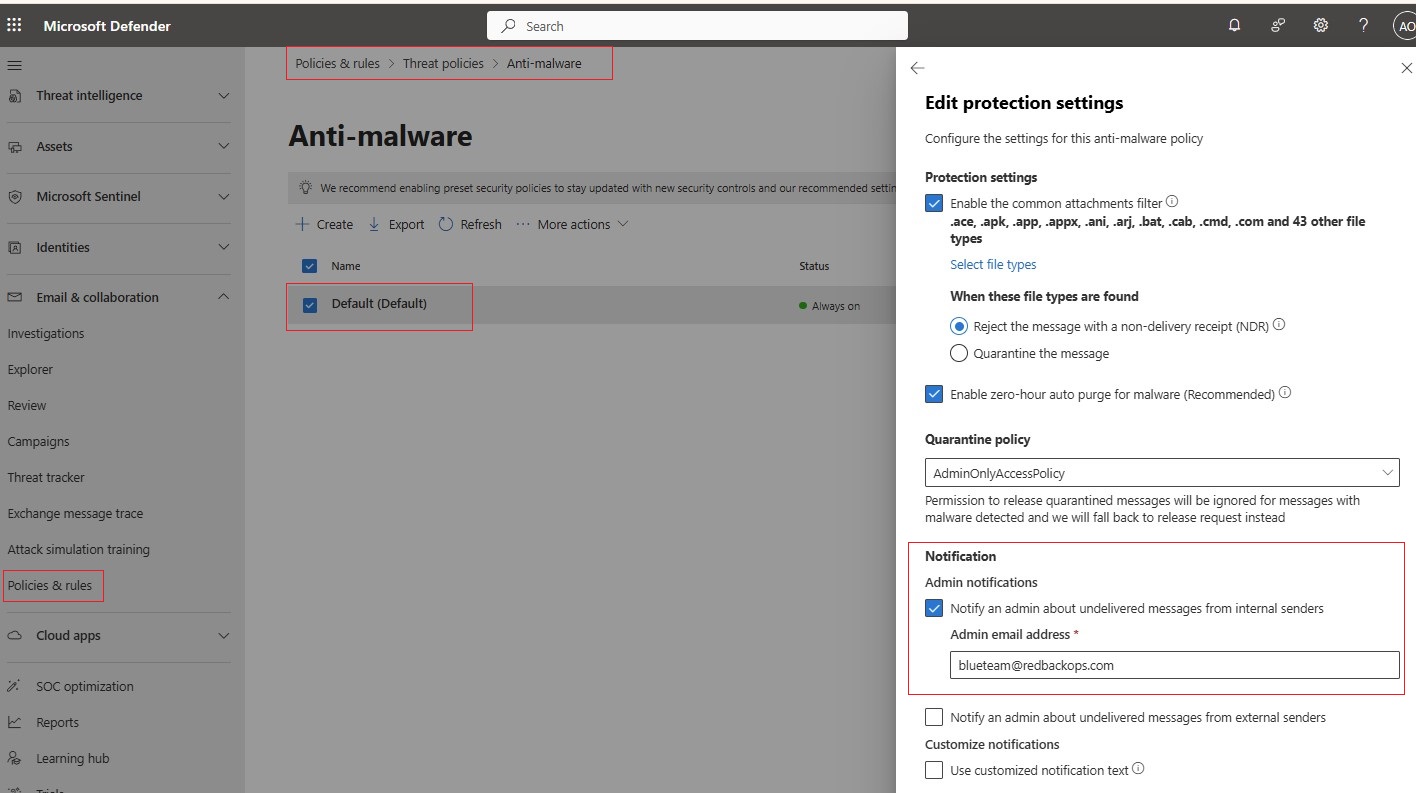
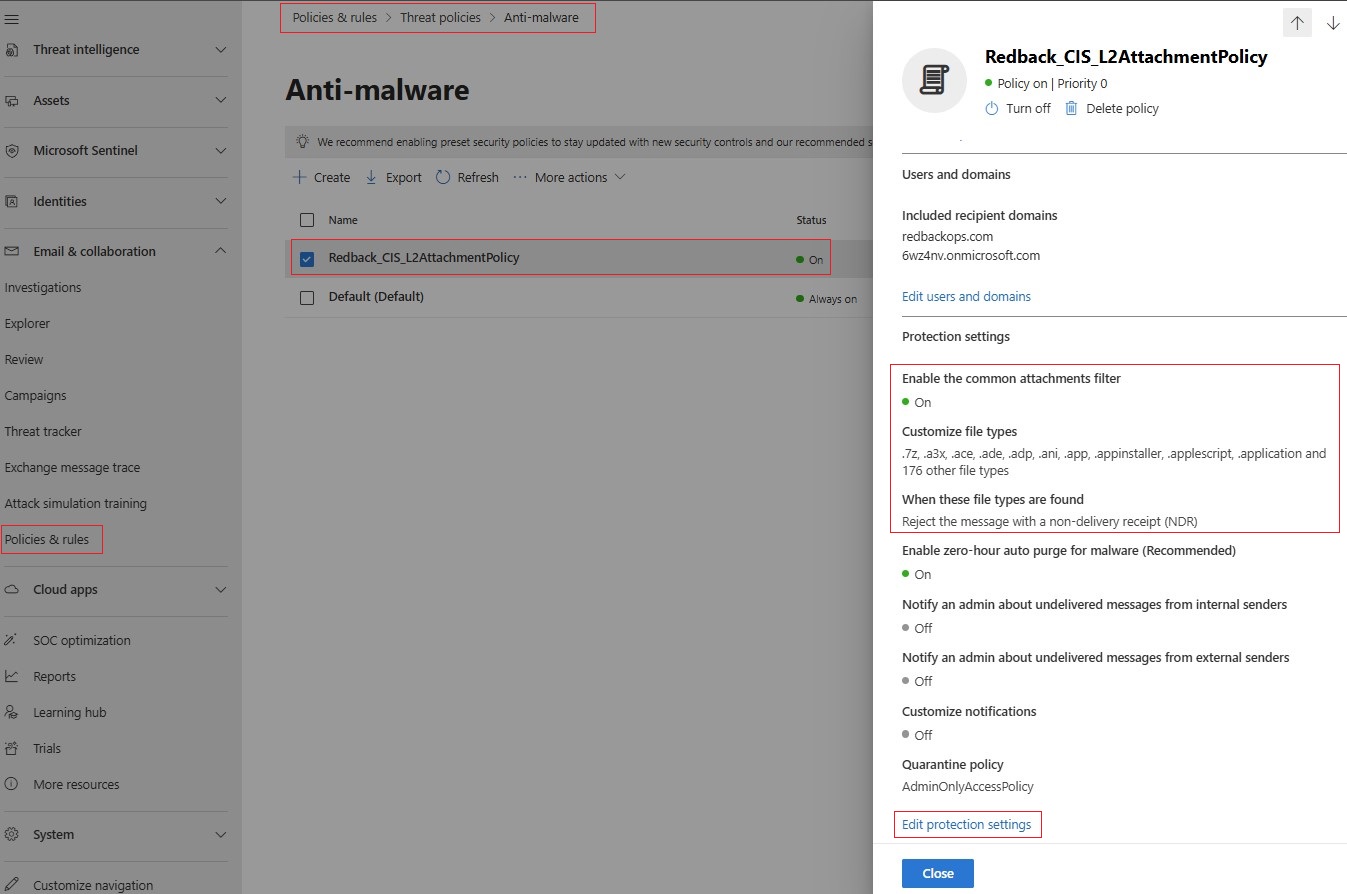
| Anti-Malware Policy | This policy: • Enables internal sender malware notifications. • Creates an anti-malware policy that blocks 186 malicious file types. | 2.1.3, 2.1.11 |
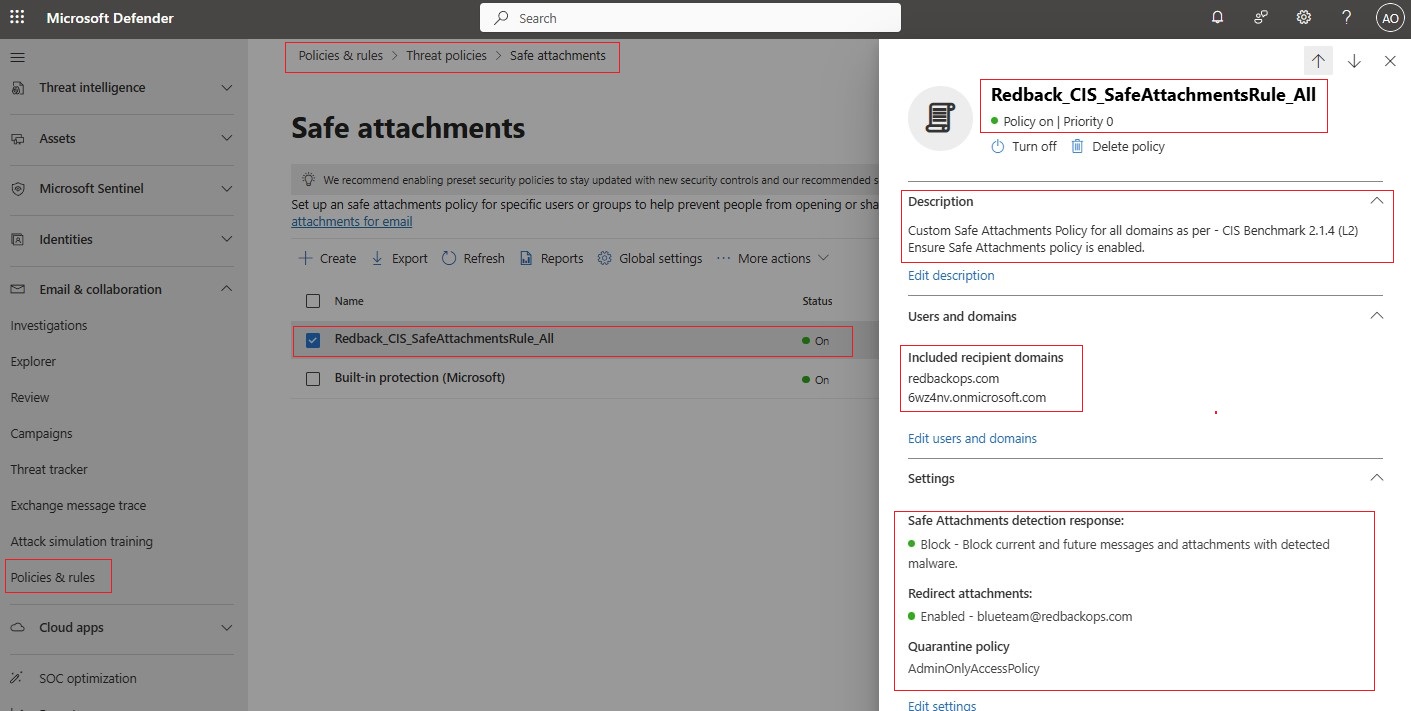
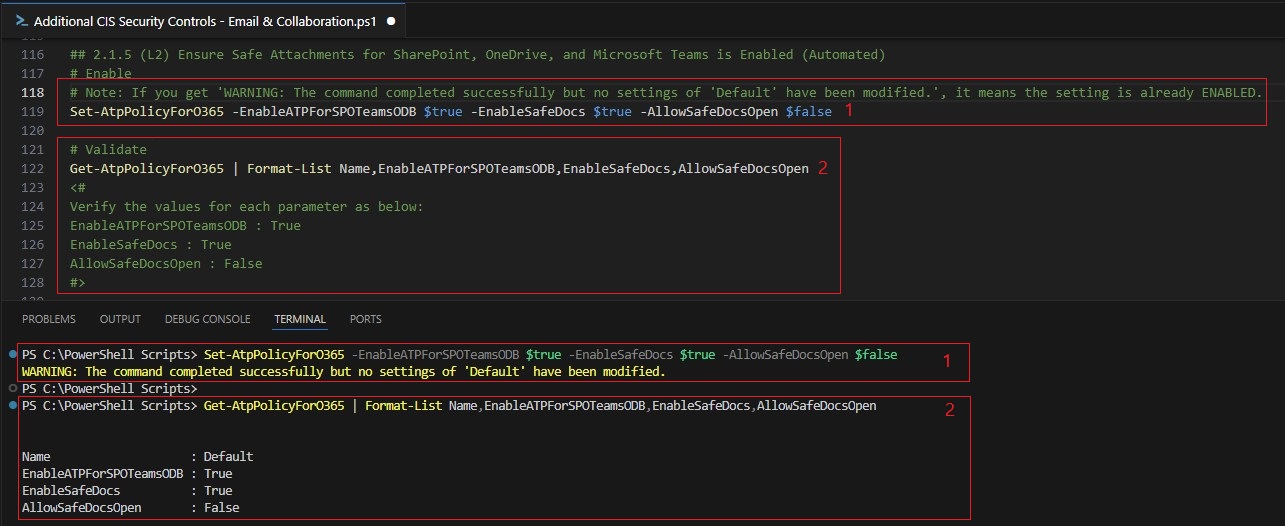
| Safe Attachments Policy | This policy: • Ensures Safe Attachments Policy is enabled. • Blocks malicious files, redirects them to an admin quarantine, and extends attachment protection to SharePoint, OneDrive and Teams. | 2.1.4, 2.1.5 |
| Safe Links Policy | This policy enables Safe Links for emails, Teams and Office applications, including protection such as URL click tracking, URL scanning, URL rewriting, and blocking user click-through on detected malicious links. | 2.1.1 |
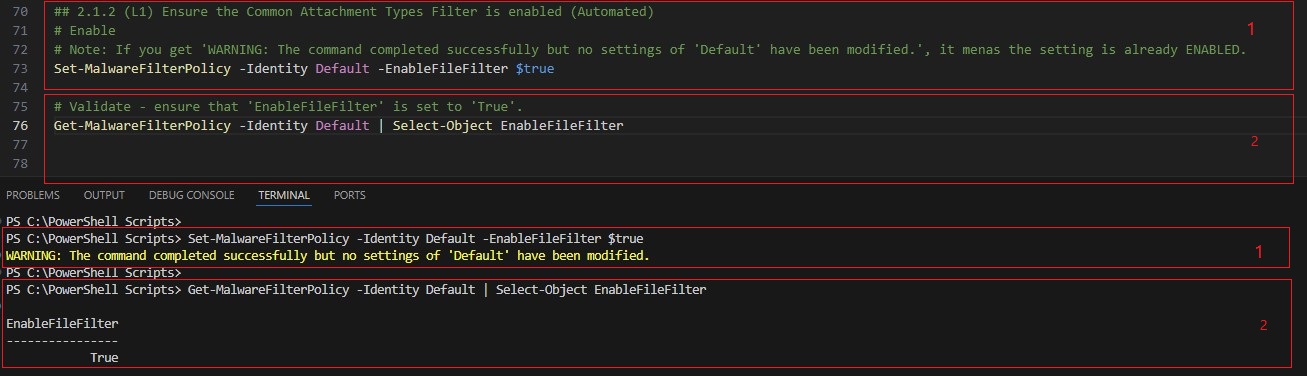
| Common Attachment Types Filtering | This policy enables the default anti-malware policy’s file type filter to block common high-risk attachment types. | 2.1.2 |
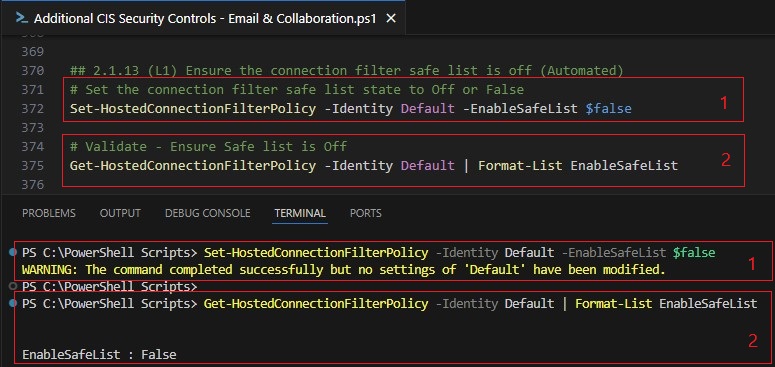
| Connection Filtering Policy | This policy: • Ensures no IP addresses are listed in the connection filtering policy to prevent filter bypass. • Disables the safe sender list in the connection filter policy to prevent filter bypass. | 2.1.12, 2.1.13 |
10. Implement additional security controls based on CIS Foundations Benchmark guidelines
Each control listed in the deliverables section was implemented step-by-step in a sequential order using PowerShell cmdlets.
11. Validate additional security controls based on CIS Foundations Benchmark guidelines
As for validation, each control was validated using PowerShell cmdlets and via GUI validation immediately after implementation. The validation included checks for:
- Policy creation and enablement status
- Scope assignment to all accepted domains
- Rule and policy priorities, and expected behaviours
- Flagging any missing configuration values and resolving any configuration anomalies.
Validation details and screenshot references are listed below.
Implementation and Validation with Screenshot References
PowerShell Setup Steps
Before implementing the controls, the following PowerShell setup steps were implemented:
- Installed the ExchangeOnlineManagement PowerShell module.
- Set execution policy to ‘Bypass’ for the current session.
- Imported the module.
- Connected using an account with 'Global Administrator' or 'Exchange Administrator' permissions.
- Enabled organization customization using
Enable-OrganizationCustomization. - Verified that
IsDehydratedwas set toFalse.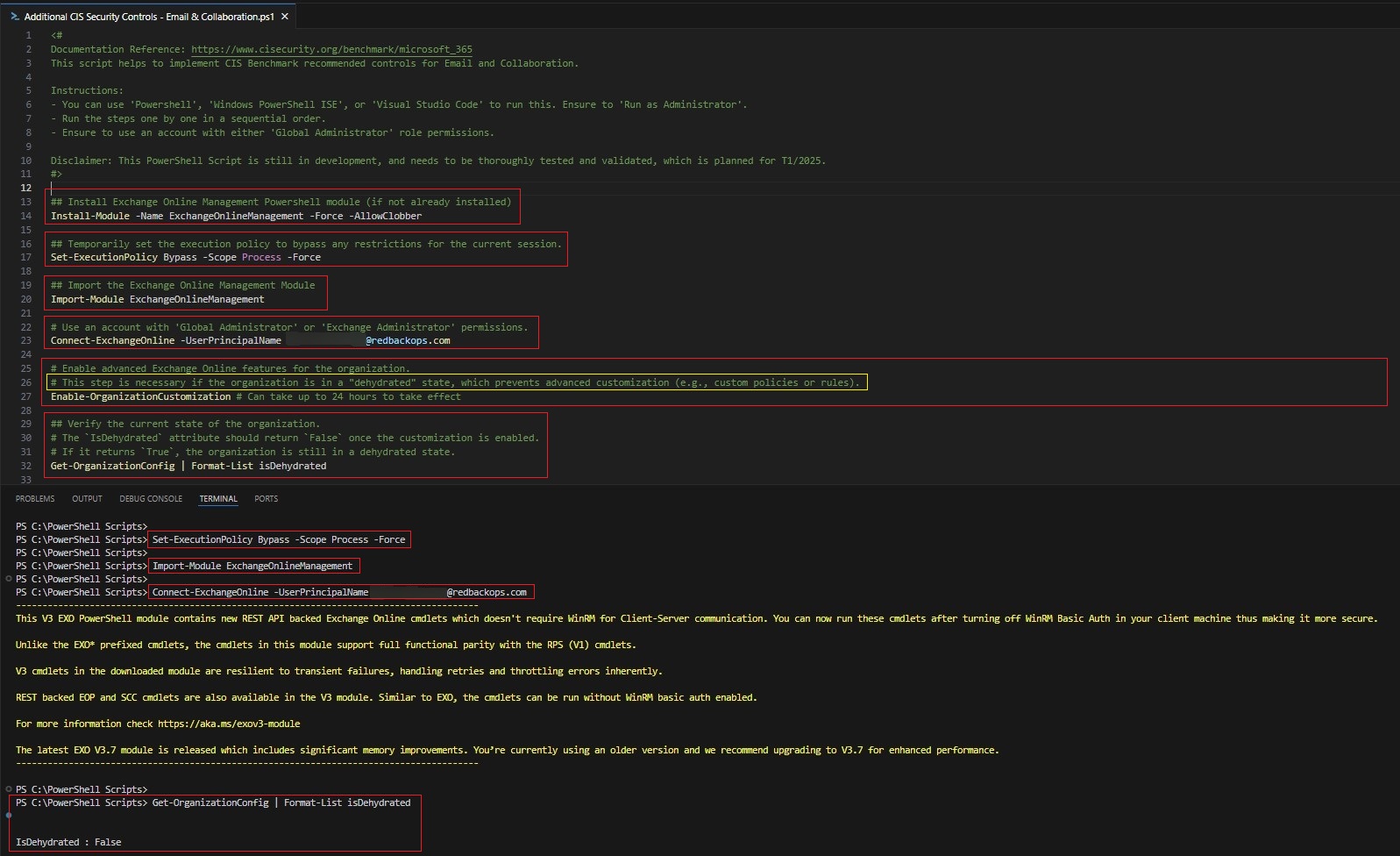
10.1. Anti-phishing Policy



10.2. Anti-spam Policy

10.3. Anti-malware Policy








10.4. Safe Attachments Policy



10.5. Safe Links Policy




10.6. Common Attachment Types Filtering Policy

10.7. Connection Filtering Policy